Why Cybercriminals Target Small and Mid-Sized Companies (And How They Get In)
The uncomfortable truth about modern cyber attacks and what your business needs to know

If you think your company is too small to be a target, think again. Cybercriminals aren't just hunting Fortune 500 companies anymore. Small and mid-sized businesses (from boutique hotels and luxury resorts to art galleries, restaurants, e-commerce stores, and professional services firms) have become the preferred targets, and the statistics are sobering.
In 2023, 46% of all cyber breaches impacted businesses with fewer than 1,000 employees. Even more alarming, 82% of ransomware attacks targeted these same organizations. The average cost? $1.3 million in losses, with ransomware attacks averaging $5.13 million.
The Goldilocks Principle: Why You're Just Right
Small and mid-sized companies occupy a dangerous middle ground. You're large enough to have valuable assets worth stealing, but often small enough to lack dedicated security teams. Whether you're running a resort processing hundreds of credit card transactions daily, an art gallery maintaining client databases, a restaurant managing online reservations, or an e-commerce store handling customer information, you process sensitive data that makes you profitable to attack.
More importantly, you're typically running business-critical applications without the security oversight that enterprise companies maintain. Your booking systems, payment portals, customer management platforms, and inventory systems often contain vulnerabilities that have never been professionally tested. A boutique hotel's reservation system, a retail shop's e-commerce platform, or a restaurant's point-of-sale system can all harbor exploitable weaknesses.
Attackers know this. They know you have the budget for technology but may not have allocated resources specifically for security assessment. You're profitable enough to pay a ransom, but unlikely to have the sophisticated defenses that would make the attack too difficult.
Real-World Impact Across Industries
The threat spans every sector of small and mid-sized business:
- Hotels and Resorts: Booking systems, guest Wi-Fi networks, and property management software create multiple attack vectors. A breach exposes guest credit cards, personal information, and reservation details.
- Restaurants and Cafés: Point-of-sale systems, online ordering platforms, and reservation apps handle payment data hourly. One compromised terminal can leak thousands of credit cards.
- Retail and Art Shops: E-commerce platforms, inventory systems, and customer databases contain purchasing history and payment information. Attackers target both online storefronts and in-store payment terminals.
- Professional Services: Law firms, accounting practices, and consulting agencies manage confidential client data. A breach doesn't just cost money. It destroys client trust and professional reputation.
- Healthcare Clinics: Medical practices and dental offices store protected health information (PHI) and insurance details. HIPAA violations compound the financial damage of breaches.
- Real Estate Agencies: Transaction details, client financial information, and property data make agencies attractive targets for wire fraud and identity theft.
How Attackers Actually Get In
Forget the Hollywood version of hooded hackers typing furiously in dark rooms. Real attacks are methodical, patient, and surprisingly straightforward. Here's how they actually work:
1. Application Vulnerabilities: The Front Door You Left Open
Your web applications are running 24/7, accessible to anyone with an internet connection. Many contain security flaws that attackers can exploit within minutes of discovery. For small and mid-sized businesses, these vulnerable applications include:
- Hotel booking apps and reservation systems
- Restaurant online ordering and delivery platforms
- E-commerce storefronts and payment gateways
- Appointment scheduling systems for salons, clinics, and service providers
- Customer portals and member login areas
- Event registration and ticketing platforms
Common vulnerabilities in these systems include:
- SQL Injection: Attackers manipulate database queries to extract sensitive information or gain unauthorized access to customer records, credit cards, and booking details
- Cross-Site Scripting (XSS): Malicious scripts injected into your application can steal user credentials, session tokens, or payment information from your customers
- Broken Authentication: Weak password policies or session management flaws allow account takeovers, giving attackers access to customer accounts and administrative panels
- API Vulnerabilities: Improperly secured APIs expose business logic, inventory data, pricing information, and sensitive customer data
These aren't theoretical risks. They exist in production applications right now, waiting to be discovered. The question isn't if vulnerabilities exist in your booking system, payment portal, or customer database, but whether you'll find them before attackers do.
2. Social Engineering: Exploiting Your Most Valuable Asset
Your employees aren't a weakness, unless they're untrained. Attackers use sophisticated phishing campaigns that bypass technical controls entirely. A single clicked link or shared credential can provide complete network access.
Modern phishing attacks are personalized, contextual, and frighteningly convincing. They reference real projects, mimic executive communication styles, and create urgency that bypasses rational decision-making.
3. Third-Party Dependencies: The Supply Chain Weakness
Every vendor integration, every cloud service, every software library represents a potential entry point. Small and mid-sized businesses often rely heavily on third-party services:
- Payment processors (Stripe, Square, PayPal)
- Booking and reservation platforms (OpenTable, Resy, booking.com integrations)
- CRM systems (HubSpot, Salesforce, Zoho)
- Email marketing platforms (Mailchimp, Constant Contact)
- Website builders and e-commerce platforms (Shopify, WooCommerce, Squarespace)
- Analytics and tracking tools (Google Analytics, Facebook Pixel)
Attackers increasingly target the software supply chain because it's often less defended than your primary infrastructure. When your payment processor, CRM system, or analytics platform gets compromised, your security controls are irrelevant. The attacker is already inside through a trusted channel.
4. Infrastructure Misconfigurations: The Unforced Errors
Cloud services make deployment easy, but proper security configuration requires expertise. Common mistakes include:
- Publicly accessible databases with default credentials
- Storage buckets with incorrect permission settings
- Unpatched systems running critical services
- Exposed administrative interfaces
The Attack Timeline: What Actually Happens
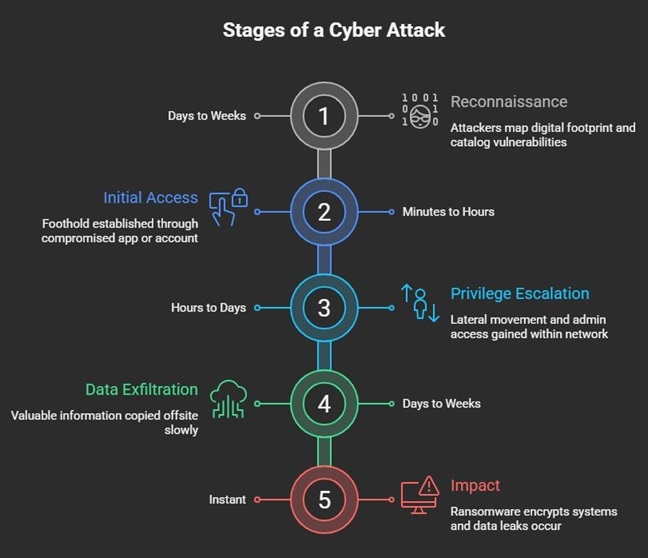
Understanding how attacks unfold helps illustrate why prevention is critical:
- Reconnaissance (Days to Weeks): Attackers identify your digital footprint, map your infrastructure, and catalog potential vulnerabilities. They're patient.
- Initial Access (Minutes to Hours): Using discovered vulnerabilities or social engineering, they establish their first foothold. This often happens through a single compromised application or user account.
- Privilege Escalation (Hours to Days): They expand access, moving laterally through your network, gaining administrative privileges, and identifying valuable assets.
- Data Exfiltration (Days to Weeks): They extract valuable information slowly to avoid detection. Customer databases, financial records, intellectual property. Everything is copied offsite.
- Impact (Instant): Finally, they execute. Ransomware encrypts your systems. Data appears on leak sites. Operations halt. The damage that took weeks to prepare happens in minutes.
The sobering reality? Most organizations only discover the breach at step 5, long after attackers have achieved all their objectives.
The Real Cost Isn't Just Money
While the financial impact averages $1.3 million, the true cost extends far beyond immediate monetary loss. For small and mid-sized businesses, the impact can be devastating:
- Business Disruption: Operations halt while systems are restored. Hotels can't process reservations. Restaurants lose online orders. Retail stores can't complete sales. Revenue stops completely.
- Reputation Damage: Customer trust, built over years, evaporates overnight. A hotel that leaks guest credit card data loses bookings. A restaurant that exposes customer information sees reservations plummet. Competitors capitalize on your vulnerability.
- Legal Liability: Regulatory fines, lawsuits, and compliance violations compound the financial damage. PCI-DSS violations for payment data, GDPR fines for customer information, or HIPAA penalties for healthcare practices.
- Recovery Resources: Your small team spends months rebuilding systems instead of serving customers and growing the business. Staff who should be focused on hospitality, sales, or client service are dealing with security incidents.
- Competitive Disadvantage: While you're recovering, competitors are advancing. That boutique hotel down the street that invested in security keeps operating normally.
- Insurance Challenges: Many small businesses discover their general liability policies don't cover cyber incidents, leaving them fully exposed to breach costs.
By The Numbers
- 46% of breaches impact small and mid-sized companies (under 1,000 employees)
- 82% of ransomware targets small and mid-sized businesses
- $1.3M average cost per cyber incident
- $5.13M average ransomware attack cost
- 60% of small businesses close within 6 months of a major cyber attack
What Professional Security Assessment Reveals
When security professionals assess small and mid-sized companies across hospitality, retail, food service, and professional services, they consistently find issues across three categories:
Critical Vulnerabilities
High-severity flaws that provide immediate access to sensitive data or systems. These require urgent remediation because they're actively being exploited in the wild. Examples include unpatched payment systems in restaurants, exposed customer databases in hotel booking apps, or authentication bypasses in e-commerce platforms.
Configuration Weaknesses
Security settings that don't follow best practices. While not immediately exploitable, they create unnecessary risk and reduce your defensive depth. Common issues include default passwords on Wi-Fi networks, misconfigured cloud storage exposing customer data, or improperly secured administrative panels.
Architecture Gaps
Fundamental design issues that require strategic remediation. These often stem from rapid growth without security considerations, such as connecting new locations to insecure networks, integrating third-party booking systems without proper vetting, or expanding e-commerce without security architecture planning.
The value isn't just finding problems, it's understanding their business impact and getting a prioritized roadmap for remediation. Not all vulnerabilities are equally critical. Professional assessment helps you allocate limited resources effectively, focusing first on the issues that actually threaten your operations and customer data.
Beyond Compliance: Why Checkboxes Aren't Enough
Many companies treat security as a compliance exercise. They implement required controls, pass audits, and assume they're protected. This is dangerous thinking.
Compliance frameworks establish minimum baselines, but attackers aren't constrained by compliance requirements. They exploit real vulnerabilities, regardless of whether you checked all the boxes.
Effective security requires understanding how attackers actually operate, not just satisfying auditor requirements. It means testing your defenses the way adversaries will. Through actual application security testing, penetration testing, and vulnerability assessment.
The Proactive Approach: Finding Weaknesses First
The fundamental principle is simple: find and fix vulnerabilities before attackers exploit them. This requires three things:
- Regular Assessment: Your application environment changes constantly. New code, new integrations, new services. Each introduces potential vulnerabilities. One-time testing isn't sufficient.
- Real-World Testing: Automated scanning catches known issues, but manual penetration testing discovers the complex vulnerabilities that actually matter. Professional testers think like attackers.
- Actionable Remediation: Finding vulnerabilities is useless without clear guidance for fixing them. You need prioritized recommendations with business context.
What Makes an Effective Security Partner
Not all security assessments are created equal. Effective security partners understand that you're running a business, not a security research lab. They provide:
- Business Context: Technical findings translated into business impact. Understanding which vulnerabilities actually threaten your operations.
- Practical Guidance: Remediation recommendations that work within your technical constraints and resource limitations.
- Ongoing Support: Security isn't a one-time project. Continuous engagement to verify fixes and assess new changes.
- Manual Expertise: Real security professionals who understand application logic, business processes, and attack techniques, not just automated scan results.
The Investment That Protects Everything Else
Consider the economics: professional security assessment costs a fraction of a single breach. You're investing thousands to avoid losing millions. More importantly, you're protecting:
- Customer relationships built over years
- Revenue streams that fund growth
- Intellectual property that differentiates your business
- Operational continuity that enables execution
- Market position that took years to establish
The question isn't whether you can afford security assessment. It's whether you can afford not to.
Taking the Next Step
Cybercriminals are targeting small and mid-sized companies because the math works in their favor. Whether you run a hotel, restaurant, retail shop, professional practice, or e-commerce business, you have valuable assets but often lack dedicated security teams. Your booking systems, payment platforms, and customer databases process sensitive data without the rigorous testing that enterprise companies mandate.
But this isn't inevitable. Professional security assessment levels the playing field. It reveals vulnerabilities in your reservation systems, point-of-sale terminals, and web applications before attackers exploit them. It provides the insights needed to make informed security investments tailored to your industry and size. Most importantly, it shifts you from reactive victim to proactive defender.
The threats are real, the statistics are sobering, and the costs of breach are severe. But understanding these realities is the first step toward effective protection.
Your hotel booking apps, restaurant ordering platform, retail payment system, or customer portal may contain serious vulnerabilities right now. The only question is who discovers them first. You or an attacker.
Ready to Secure Your Digital Infrastructure?
CrisisWall provides comprehensive security assessment services tailored for small and mid-sized businesses across all industries. Whether you operate hotels, restaurants, retail stores, professional practices, or e-commerce platforms, we combine manual application security testing, vulnerability assessment, and penetration testing to identify and help remediate security gaps before they become breaches.
Our services include:
- Manual application security assessment for booking systems, e-commerce platforms, payment gateways, and customer portals
- Infrastructure vulnerability assessment for hotels, restaurants, retail operations, and service businesses
- Adversary simulation to test your defenses against real-world attack techniques targeting small and mid-sized businesses
- Detailed reporting with prioritized, actionable remediation guidance tailored to your industry and budget
- Confirmatory assessments to verify fixes and maintain security posture across all locations
Ready to secure your infrastructure?
Don't wait for a breach to discover your vulnerabilities. Contact us today at secure@crisiswall[.]com to discuss how we can help secure your hotel, restaurant, retail store, or business operations.